java.rmi.server
Class UnicastRemoteObject
java.lang.Objecthttp://docs.oracle.com/javase/1.5.0/docs/api/java/rmi/server/UnicastRemoteObject.htmljava.rmi.server.RemoteObject
java.rmi.server.RemoteServer
java.rmi.server.UnicastRemoteObject
rmi tutorial
http://www.slideshare.net/junyuo/a-short-java-rmi-tutorial
http://www.youtube.com/watch?v=ILeAeFZOkMI
java.net
Class InetAddress
java.lang.Objectjava.net.InetAddress
http://docs.oracle.com/javase/1.5.0/docs/api/java/net/InetAddress.html
The InetAddress Class
The InetAddress class is a utility class that represents an IP address, which is either a 32-bit or 128-bit unsigned number used by Internet Protocol (IP). The protocols such as Transmission Control Protocol (TCP), User Datagram Protocol (UDP), and Stream Control Transport Protocol (SCTP) are built on top of IP. The instance of this class consists of an IP address and possibly its corresponding host name. The class converts numeric addresses to host names, and vice versa. The other networking classes that you have studied previously, such as Socket and ServerSocket, use this class for identifying hosts.The class does not have any public constructors, which means you cannot create any arbitrary addresses. All created addresses must be checked with DNS (Domain Name System). To create an InetAddress object, you must use one of the available factory methods. ThegetLocalHost factory method returns the InetAddress object that represents the local host. The getByName method accepts the host name as its parameter and returns the corresponding InetAddress object. Both methods throw an UnknownHostException if they are unable to resolve the host name. The getAllByName factory method returns an array of InetAddress objects that represent all the addresses the given name resolves to—note that DNS mappings allow you to associate a single name with a set of machines (IP addresses). This method may throw anUnknownException like the other two methods if it cannot resolve the name to at least one address.The class provides various getter methods that return the host name, address, and so on. The isMulticastAddress method checks whether theInetAddress is an IP multicast address. Inet4Address and Inet6Address are the two direct, known subclasses of this class. As the name indicates, Inet4Address represents an IP version 4 address and Inet6Address represents an IP version 6 address. For so many years, we have been using IPv4 addresses that consist of four parts—each being a byte of data. The IPv6 address consists of eight 16-bit pieces and will soon be in use as the Internet keeps growing.We have used a variation of the class InetSocketAddress in our earlier examples while connecting to a remote server. The simple example given in Listing 20-9 illustrates the use of this class.Listing 20-9 DNS Resolution ApplicationIn the main method, we call the getAllByName static method of the InetAddress class. The method takes a host as the parameter and returns an array of the associated IP addresses. First, we list out all servers hosted by Google and then by CNN. At the end, we list out the IP address of our local machine. When you run this application, you will see output similar to the following (note that by the time you run this code, Google/CNN might have changed/added a few servers):From this output, you can see that Google has hosted their website on five different IPs, whereas CNN hosts their website on six known servers. The output shows that the local machine has only one IP associated with it (which, of course, goes without saying).
Managed File Transfer and Network Solutions
http://www.jscape.com/blog/bid/80512/Active-v-s-Passive-FTP-Simplified
When a client experiences problems when connecting to your FTP server, one thing you might want to look into is whether you've set your FTP data transfer mode to either active or passive.Active and passive are two possible modes that an FTP connection can operate on. Taking into consideration the network configurations and security controls in place, you should choose one mode over the other.But before we discuss which mode is best for what scenario, let's first talk about the basics of these two modes, which can best be explained if we start our discussion with the two channels an FTP session normally has.FTP command channel and data channel
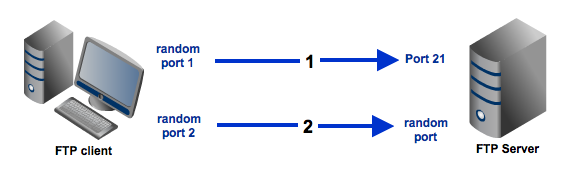
A typical FTP session operates using two channels: a command (or control) channel and a data channel. As their names imply, the command channel is used for transmitting commands as well as replies to those commands, while the data channel is used for transferring data.Unless you configure your FTP server differently, you will normally set your command channel to use port 21. The port you'll use for the data channel, on the other hand, can differ depending on which data transfer mode you choose. If you choose active mode, then the data channel will normally be port 20. But if you choose passive mode, then the port that will be used will be a random port.Note that the ports we are referring to here up to this point are only the ports on the server side. We'll include client-side ports in our discussion in a short while.Active mode FTP
Among the two modes, Active mode is the older one. It was the mode introduced in the early days of computing when mainframes were more common and attacks to information security were not as prevalent.Here's a simplified explanation on how an active mode connection is carried out, summarized in two steps. Some relevant steps (e.g. ACK replies) have been omitted to simplify things.
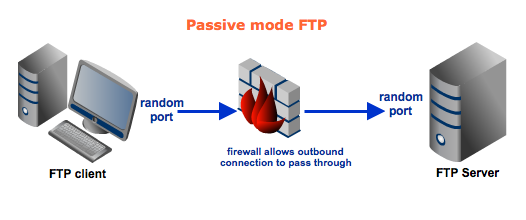
Passive mode FTP
In passive mode, the client still initiates a command channel connection to the server. However, instead of sending the PORT command, it sends the PASV command, which is basically a request for a server port to connect to for data transmission. When the FTP server replies, it indicates what port number it has opened for the ensuing data transfer.Here's how passive mode works in a nutshell:
Active mode vs Passive mode - which is more suitable for you?
There's a reason why I opted to simplify those two diagrams above. I wanted to focus on the main difference between active mode and passive mode FTP data transfers. If you compare those two diagrams, one of the things that should really stand out are the opposing directions at which thesecond arrows (which also represent the data channels) are pointing to.In this section, we'll focus on those second arrows and the ports associated with them.In the active mode, the second arrow is pointing to the client. Meaning, the client initially specifies which client-side port it has opened up for the data channel, and the server initiates the connection.By contrast, in the passive mode, the second arrow is pointing to the server. Here, the server specifies which server-side port the client should connect to and the client initiates the connection.There shouldn't be any problem had there not been any firewalls in existence. But threats to information security are on the rise and hence the presence of firewalls is almost always a given. In most cases, clients are located behind a firewall or a NAT (which basically functions like a firewall). In such cases, only a select number of predefined ports are going to be accessible from the outside.Remember that in an active mode configuration, the server will attempt to connect to a randomclient-side port. So chances are, that port wouldn't be one of those predefined ports. As a result, an attempt to connect to it will be blocked by the firewall and no connection will be established.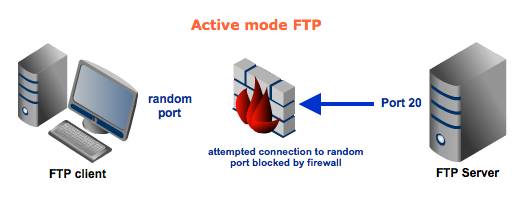 In this particular scenario, a passive configuration will not pose a problem. That's because the client will be the one initiating the connection, something that a client-side firewall won't have any problem with.Of course, it's possible for the server side to have a firewall too. However, since the server is expected to receive a greater number of connection requests compared to a client, then it would be but logical for the server admin to adapt to the situation and open up a selection of ports to satisfy passive mode configurations.
In this particular scenario, a passive configuration will not pose a problem. That's because the client will be the one initiating the connection, something that a client-side firewall won't have any problem with.Of course, it's possible for the server side to have a firewall too. However, since the server is expected to receive a greater number of connection requests compared to a client, then it would be but logical for the server admin to adapt to the situation and open up a selection of ports to satisfy passive mode configurations.Security considerations when setting up passive FTP
As explained earlier, if you're administering an FTP server, it would be best for you to configure your server to support passive mode FTP. However, you should bear in mind that in doing so, you would be making your system more vulnerable to attacks. Remember that, in passive mode, clients are supposed to connect to random server ports.Thus, to support this mode, not only should your server have to have multiple ports available, your firewall should also allow connections to all those ports to pass through!But then the more open ports you have, the more there will be to exploit. To mitigate the risks, a good solution would be to specify a range of ports on your server and then to allow only that range of ports on your firewall.Where to set up passive port range in JSCAPE MFT Server
For those of you who are already using JSCAPE MFT Server, you can specify a range of ports for your passive mode FTP connections by going to Services > FTP/S > Passive port range in your JSCAPE MFT Server Manager. Because low ports (particularly those < 1024) are reserved, choose a high port range (i.e. large numbers). For example, from 5000 to 6000. For better security, don't just copy the example. Use your own!In the event that the IP address your server uses in responding to requests for passive connections is not routable via the Internet, you'll need to enter your public IP address in the Passive IP field.JSCAPE MFT Server is a file transfer solution that supports more than just FTP. You can take a free trial now.



No comments:
Post a Comment